Social Media Hacking Statistics 2024: Alarming Trends Revealed
Social media has done a great job of making everyone’s life faster and easier. It gave you direct and constant communication with loved ones, access to valuable information and knowledge in real-time, and different ways to stay entertained. However, it also comes with a price, especially if you take your cyber security measures lightly.
The world has gone digital in almost every aspect of life, and sadly, criminals have found their way into the virtual world, too. Hacking other people’s private accounts is a vicious act that has been around ever since the beginning of the internet. Now that social media accounts are more valuable than ever for holding personal and financial information, they have become the biggest target of hackers.
Although some believe hacking doesn’t always come with malicious intent, the term has always been painted negatively and continues to be one form of cybercrime. Learning about the detrimental consequences of leaving your cyber security vulnerable and how social media hacking can be more damaging than you may think is essential.
Social media hacking refers to the unauthorised access, manipulation, or control of another user’s social media accounts or personal data. Unlike general “hacking,” which can target any computer system, social media hacking zeroes in on platforms like Facebook, Instagram, Twitter, LinkedIn, and others where individuals and businesses store sensitive information. Below are key points that define the core nature of social media hacking:
- Unauthorised Access:
Hackers exploit vulnerabilities—such as weak passwords or software flaws—to gain unauthorized access to a target’s account.
- Information Theft:
Once inside, hackers can steal personal details, messages, or financial data. These stolen credentials may then be sold on the dark web or used to commit further fraud.
- Impersonation and Control:
Malicious actors may impersonate the account owner to message friends or followers, spread harmful links, or damage a brand’s reputation.
- Varied Motives:
The intent behind social media hacking ranges from financial gain and identity theft to personal revenge, espionage, or simply “digital vandalism.”
- Common Attack Vectors:
Methods include phishing emails, malicious links in direct messages, weak password guessing, and social engineering tactics that trick users into sharing confidential details.
By focusing specifically on social media platforms, hackers often have direct access to a wealth of personal or corporate information, making it easier to orchestrate large-scale data breaches or targeted attacks. Ultimately, robust cyber security practices—such as using strong passwords and enabling multi-factor authentication—are essential to reduce the risk of social media hacking.
The Basic Concept of Hacking
Hacking is hijacking someone’s digital accounts or gaining unauthorised access to computer systems to compromise performance and cause damage. It’s an illegal activity that can be taken legal action against in many countries. The most critical part is that more than a few hacking techniques are growing stronger daily.
Cybercriminals develop new methods every day to carry out their malicious plans. Their objectives could include doxing your private information in public, stealing financial information, leaking confidential data, or holding your data for ransom. The motives behind such acts can significantly vary from one person to another.
We’ve compiled shocking statistics about social media hacking that will compel you to choose the maximum cybersecurity parameters to protect yourself.
- 70% of Instagram and Facebook users were locked out of their accounts, while 71% had the hackers impersonate and contact their friends.
- In 2023, 25% of Facebook accounts were hijacked, while the hacking percentage of Instagram accounts reached 85%.
- Facebook accounts are the most compromised account types in the United States, reaching around 67,941 every month.
- Instagram ranks second in the hacking processes, reaching an average of 36,222 monthly accounts.
- Gmail and Microsoft seem to be the least hacked social media platforms, with an average of 4,921 and 4,000 monthly searches, respectively.
- During the pandemic, 70% of data breaches occurred in 2020, when cybercrime peaked the most.
- The most extensive data breach happened in 2013 when Yahoo compromised over 3 billion accounts.
Recent Statistics of the Most Common Attacks
- Phishing attacks have increased by 130.5% since 2017 and are still rising.
- Although social media hacking is significantly high, 94% of data and information breaches are caused by user errors.
- 17% of hackers use malware to compromise systems.
- Error cases cause 96% of breaches in smartphone devices, while 3% happen due to the usage of high-risk apps.
- During the pandemic, ransomware attacks peaked the most, reaching an 800% increase due to the rise in remote work.
- Small businesses are more prone to cybercrime, 350% more subject to social engineering attacks than large firms.
Statistics on the Various Reasons and Motives for Hackers
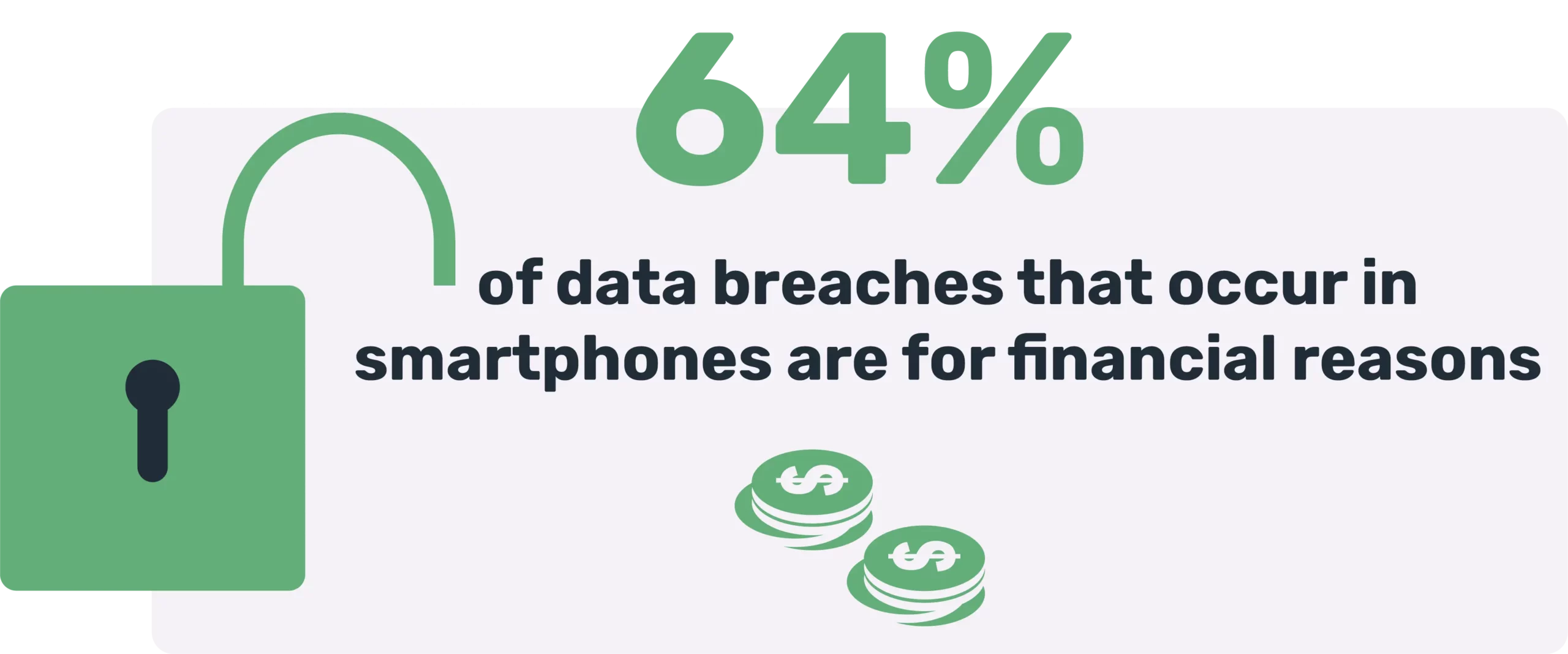
- Around 64% of smartphone data breaches occur for financial reasons.
- Social media hacking can happen for many reasons, including spying, but it only accounts for 5% of mobile device data breaches.
- Surprisingly, 78% of hackers reported committing social media hacking acts to hone their skills and compete for job opportunities.
- 51% of white hat hackers professed using hacking to enhance their skills and acquire new techniques.
- 25% of social media hacking incidents were meant for good intentions or helping others.
- While most hackers resort to data breaching to make money, 49% do it for fun.
Better safe than sorry is a saying that holds lots of truth, especially when safeguarding yourself against social media hacking. With the increasing threat of criminal attacks, it is crucial to prioritise complete protection of your social media accounts. Some damages can be irreversible once invaders become active and breach your system.
Using the right cybersecurity tools can significantly reduce the chances of social media hacking. You can proactively eliminate potential threats before they manifest. So, please walk us through the essential measures of cybersecurity that will help you fortify your defences.
Use Strong Passwords
Using the same username and password may seem convenient for all your platforms and social media accounts. However, this is a grant ticket for social media hacking, where hackers exploit and gain unauthorised access to your valuable credentials. Once they infiltrate your accounts, they can wreak havoc on your personal and financial information.
Understanding that opting for solid and resilient passwords can significantly bolster your data security is crucial. Don’t compromise your safety by settling for simple and easily guessable passwords. Safeguard your online presence and shield your sensitive data from the prying eyes of cybercriminals.
Enable Two-factor Authentication (2FA)
Implementing two-factor or multi-factor authentication is one powerful cybersecurity tool to enhance protection. This vital measure is a powerful deterrent against malicious hackers attempting to breach your system. This method requires users to present two or more pieces of evidence to access a website or application.
This electronic authentication method is akin to a double-door security system. Even when the criminal succeeds in unlocking the first door, they will be confronted with another, more resilient barrier. With two-factor authentication in place, safeguarding yourself against the perils of social media hacking becomes a reality.
Install Antivirus Software
Antivirus programs are often overlooked, but their significance cannot be overstated. To fight cybercrime threats effectively, updating and installing top-tier antivirus software regularly is crucial. If you don’t have one of those antivirus software programs installed on your devices, you’re making yourself an easy target for criminals waiting to strike.
These software solutions boast many functions, encompassing malware detection and elimination and fortifying your system with robust firewalls. Doing so makes your digital fortress impenetrable, shielding you against malicious cyber attackers. It’s one of the best practices to halt social media hacking attempts.
Adjust Your Privacy Settings
It’s essential to recognise the risks that come with the openness of using social media platforms. Sharing personal information on these platforms can inadvertently expose us to potential hacking attempts. It’s critical to take proactive measures to protect our privacy. One effective way is to diligently adjust our privacy settings on various social media platforms, optimising them to grant us the utmost control over who can access our information.
Also, we cannot emphasise the importance of being mindful of oversharing personal details, such as intimate photos or excessive information about our friends and families. This simple cautionary step helps safeguard us against the threat of doxxing, where our personal information may be maliciously exploited.
Update Your Software Regularly
Using outdated software leaves you at the mercy of cybercriminals, who thrive on preying on the vulnerabilities and weaknesses in your devices. The longer you stick with an old version, the more risks you expose yourself to. This is especially true for new updates, such as regularly fixing bugs that may compromise your system or leave a backdoor for your attackers to exploit.
Nonetheless, it is crucial to pay attention to update reminders of your social media applications and never ignore them. Social media hacking is more damaging than some believe. Emphasising the significance of this cybersecurity measure, it not only safeguards your privacy but also protects your sensitive data, either personal or financial.
Avoid Using Wi-Fi in Public
Remote working has become the norm today, and many of us take liberty in setting up our workstations in public spaces. While this can be fun to many, one should still be mindful of the potential risks of using public Wi-Fi. These networks found in restaurants and cafes are often unsecured, giving open backdoors for criminals to exploit.
That’s where the absolute necessity of using Virtual Private Networks (VPNs) comes into play. VPNs are essential for safeguarding your device and network, especially when connected to public networks.
Disregard Suspicious Ads and Links
Social media applications are platforms where ads and links are everywhere. While most of them are pretty benign, others are implanted by criminals to lure you into their traps. When unsuspecting victims click on these elements, their systems become vulnerable to malware infiltration, paving the way for social media hacking attempts to follow through.
Among the various tactics criminals employ, phishing is the most commonly used attack to exploit individuals and their data. Typically, criminals send spam emails, impersonating trusted sources or acquaintances, to coax recipients into sharing their private information. These spam emails may contain malicious links or infected attachments that silently await the target’s unwitting interaction.
Back Up Your Data
Data backup is a crucial aspect of cybersecurity that ensures the preservation of valuable personal information and sensitive data. It is a protective layer in a cyber-attack or a social media hacking attempt to corrupt or destroy your data. A backup allows you to retrieve your information even after an attack occurs.
However, backing up your data on a separate storage medium, including USB flash drives and/or external hard drives, is essential. This separation guarantees that your backup server remains out of reach from potential attackers. It is worth noting, though, that the continuous connection of your external storage device to the computer can pose risks of infection to both the device and your system.
Social media hacking is rising, and different techniques are used to accomplish the mission. Cybercriminals may have various motives regarding why they breach the data of some devices or compromise social media accounts. Although many do it for good reasons, hacking is still a cybercrime. Ensure you get well-versed in the different sides of social media hacking methods to recognise when something fishy is happening.
Types of Hacking Techniques
Hackers employ various techniques to gain unauthorized access to social media accounts and compromise user data. Here are some common types of hacking techniques:
1. Phishing
- Tricking users: Phishing attacks involve sending deceptive emails or messages that appear to be from legitimate sources, such as banks, social media platforms, or friends. 1. cyberinspired.com cyberinspired.com
- Obtaining credentials: Phishing attempts often trick users into clicking on malicious links or entering their login credentials on fake websites.
- Social engineering: Hackers may use social engineering tactics to manipulate users into revealing sensitive information.
2. Brute-Force Attacks
- Automated guessing: Brute-force attacks involve systematically trying different combinations of usernames and passwords to gain access to an account.
- Weak passwords: Accounts with weak or easily guessable passwords are particularly vulnerable to brute-force attacks.
3. Malware
- Malicious software: Malware is any malicious software designed to harm computer systems or steal data.
- Infection methods: Malware can be spread through infected emails, malicious links, or downloads.
- Data theft: Once installed, malware can steal user data, including login credentials and personal information.
4. Session Hijacking
- Intercepting sessions: Session hijacking involves taking over an active user session, allowing the attacker to access the user’s account without their knowledge.
- Unsecured networks: Public Wi-Fi networks and unsecured websites can make users more vulnerable to session hijacking.
5. Keylogging
- Tracking keystrokes: Keylogging software records keystrokes entered on a device, allowing hackers to capture login credentials and other sensitive information.
- Malicious software: Keylogging software can be installed through malware or other malicious techniques.
These are a few examples of hacking techniques commonly used on social media. It’s important to be aware of these threats and take steps to protect your accounts from unauthorized access.
Social media hacking can have severe consequences, both personally and professionally. Here are some potential consequences:
1. Financial Loss
- Identity theft: Hackers can use stolen login credentials to access personal accounts, such as banking, credit card, or email accounts.
- Unauthorized transactions: Hackers may make unauthorized purchases or transfers using your financial information.
- Identity fraud: Stolen personal information can be used to commit identity fraud, resulting in financial damage and difficulty rebuilding your credit.
2. Identity Theft
- Compromised identity: Hackers can use your personal information to create fake accounts or impersonate you online.
- Reputation damage: Identity theft can damage your reputation and make it difficult to conduct business or personal relationships.
- Legal issues: Identity theft can lead to legal problems and financial burdens.
3. Reputational Damage
- Negative online presence: Hackers can post harmful or embarrassing content on your social media accounts, damaging your reputation.
- Loss of trust: If your accounts are compromised or used for malicious purposes, your followers may lose your trust.
- Career impact: Reputational damage can negatively impact your career, mainly if you rely on your online presence.
4. Emotional Distress
- Anxiety and stress: Being a victim of social media hacking can cause significant emotional distress, anxiety, and stress.
- Loss of control: The feeling of having your personal information and online identity compromised can be distressing and overwhelming.
Protecting your social media accounts and minimising the risk of hacking is essential. By following best practices for cybersecurity and being vigilant, you can help safeguard yourself from these potential consequences.
Why Are Instagram and Facebook Accounts Frequently Targeted?
Instagram and Facebook remain two of the most appealing targets for cybercriminals seeking quick and lucrative returns. The massive global user bases and the richness of personal information and commercial activity create an environment ripe for exploitation. Below are the key reasons these platforms attract hackers:
- Huge User Bases
With billions of monthly active users worldwide, Instagram and Facebook host endless personal data streams. This volume gives hackers unlimited opportunities to exploit vulnerabilities and launch large-scale attacks.
- Wealth of Personal and Financial Data
People often link their social media accounts to payment methods or store sensitive information—personal details, private messages, and business credentials—making these profiles a treasure trove for identity theft and fraud.
- Monetisation Potential
Influencers, brand ambassadors, and eCommerce businesses heavily rely on Instagram and Facebook for revenue. Hijacking these accounts allows hackers to redirect profits, spread malware via sponsored posts, or hold the account ransom to extort money.
- High Engagement and Trust
Friends, followers, and customers typically trust messages and content from familiar platform profiles. Once an account is hacked, attackers can impersonate users to send harmful links or phishing messages to a broader audience.
- Inadequate Security Practices
Many users still rely on weak passwords or reuse credentials across multiple sites. This lack of robust security measures—such as two-factor authentication—makes it easier for cybercriminals to compromise accounts.
By understanding these factors, businesses and individuals can better appreciate the importance of secure login practices, routine password updates, and proactive monitoring to guard against attacks on social media.
Social media platforms are crucial in protecting their users from hacking and data breaches. While they cannot guarantee complete security, they implement various measures to enhance user safety:
1. Two-Factor Authentication (2FA)
- An added layer of security: 2FA requires users to provide a second form of verification, such as a code sent to their phone or email, in addition to their password.
- Enhanced protection: 2FA significantly reduces the risk of unauthorized access, even if someone obtains your password.
2. Strong Password Requirements
- Enforced complexity: Platforms often require strong passwords, such as using a combination of uppercase and lowercase letters, numbers, and symbols.
- Password managers: Encourage users to use password managers to securely create and store complex passwords.
3. Security Updates
- Regular patches: Platforms release updates to address security vulnerabilities and improve protection.
- User education: Platforms often guide how to stay safe online and avoid falling victim to scams.
4. Data Encryption
- Protecting sensitive information: Platforms encrypt user data, making it difficult for hackers to access and understand.
- Secure storage: Encrypted data is stored securely to prevent unauthorized access.
5. Phishing Prevention
- Education and awareness: Platforms educate users about phishing scams and provide tips on identifying and avoiding them.
- Phishing filters: Platforms may use advanced techniques to detect and block phishing attempts.
6. User Reporting Tools
- Empowering users: Platforms often provide tools that allow users to report suspicious activity or content.
- Swift action: When reports are received, platforms can take swift action to investigate and address security threats.
7. Partnerships with Security Experts
- Collaboration: Platforms collaborate with cybersecurity experts to stay informed about emerging threats and best practices.
- Proactive measures: Platforms can implement proactive measures to protect their users by partnering with experts.
While social media platforms take various steps to protect user data, it’s also essential for users to practice safe online habits. This includes using strong passwords, avoiding clicking suspicious links, and being cautious about sharing personal information online.
FAQs
How Do Instagram Accounts Get Hacked?
Instagram accounts are commonly compromised through phishing emails, malicious links, or weak password practices. Hackers often send fake login prompts that mimic Instagram’s interface, tricking users into typing their credentials. Reusing the same password across multiple sites also makes it easier for attackers to gain entry if they’ve acquired the password from a less secure platform. Regularly updating passwords, using two-factor authentication, and verifying suspicious links can significantly reduce the risk.
Which Social Media App Is the Safest?
No platform is 100% immune to hacking, but some apps offer stronger security features and privacy controls than others. Look for platforms with built-in end-to-end encryption (where applicable), robust two-factor authentication, and user-friendly privacy settings. Regardless of the app, best practices—like using unique passwords and enabling login alerts—are essential to minimise threats.
What Are the Most Common Methods Hackers Use?
Phishing, social engineering, keylogging software, and password-guessing (brute force) are among the most prevalent. Hackers rely on human error—such as clicking on suspicious links or ignoring security warnings—to gain unauthorised access.